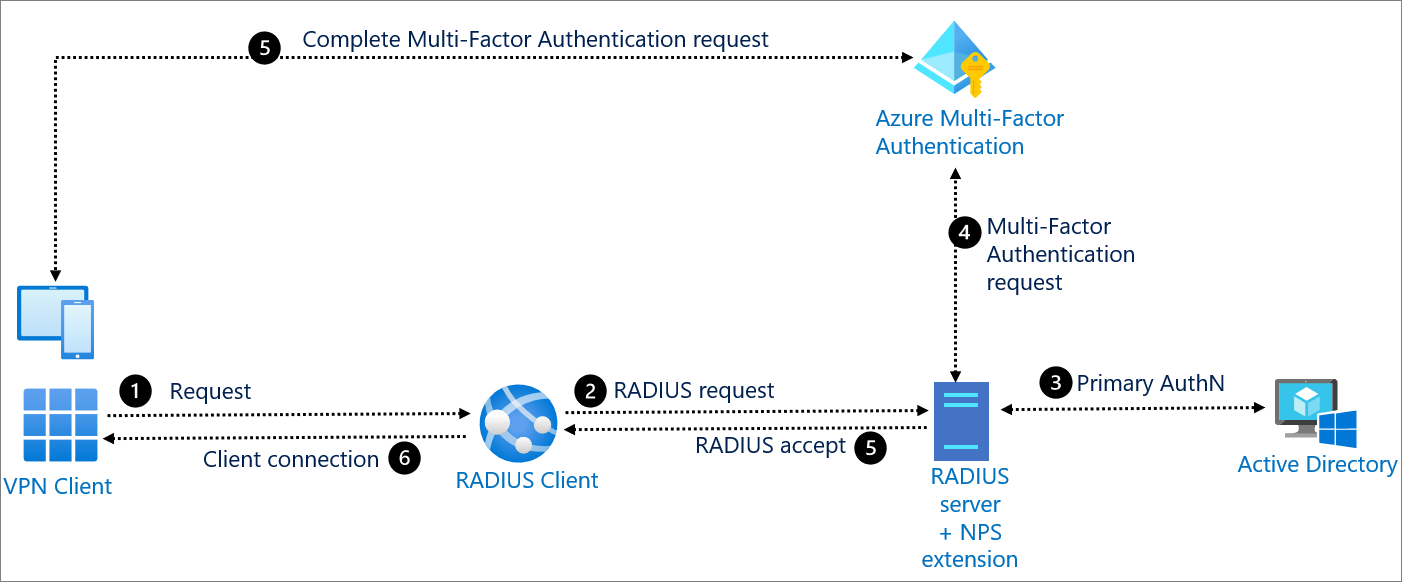
In today's digital landscape, securing user data and ensuring authorized access to resources is of paramount importance. One of the most effective methods for achieving this is through RADIUS (Remote Authentication Dial-In User Service) authentication integrated with Active Directory (AD). This combination not only streamlines the authentication process but also enhances security by centralizing user management. By utilizing RADIUS authentication with Active Directory, organizations can enforce strict access controls, monitor user activity, and maintain compliance with regulatory requirements.
The integration of RADIUS authentication with Active Directory provides a seamless experience for users while simplifying administrative tasks for IT teams. With this approach, organizations can easily manage user credentials and access privileges from a single platform. This not only reduces the risk of unauthorized access but also allows for better tracking and auditing of user actions within the network.
As businesses continue to evolve and adopt new technologies, the need for robust security measures becomes increasingly vital. RADIUS authentication combined with Active Directory offers a powerful solution to address these challenges, ensuring that only authorized users can access sensitive information and resources. In this article, we will explore the intricacies of RADIUS authentication with Active Directory, its benefits, and how to implement it effectively within your organization.
What is RADIUS Authentication and How Does it Work?
RADIUS authentication is a network protocol that provides centralized authentication, authorization, and accounting (AAA) management for users who connect and use a network service. It operates by allowing users to authenticate through a RADIUS server, which then communicates with a backend database, such as Active Directory, to verify the credentials. The process typically involves several key steps:
- User attempts to connect to the network.
- The user's credentials are sent to the RADIUS server.
- The RADIUS server checks the credentials against Active Directory.
- If the credentials are valid, access is granted; otherwise, it is denied.
Why Integrate RADIUS Authentication with Active Directory?
Integrating RADIUS authentication with Active Directory presents numerous advantages, including:
- Centralized user management: Manage all user accounts and permissions from a single location.
- Enhanced security: Implement stronger authentication methods such as two-factor authentication (2FA).
- Audit and compliance: Track user activities for regulatory compliance and security auditing.
- Scalability: Easily add or remove users as your organization grows.
How Can Organizations Implement RADIUS Authentication with Active Directory?
Implementing RADIUS authentication with Active Directory can be broken down into several steps:
- Set up a RADIUS server: Deploy a RADIUS server (such as Microsoft NPS) to handle authentication requests.
- Configure Active Directory: Ensure that all user accounts are properly set up in Active Directory.
- Establish RADIUS policies: Define authentication and access policies in the RADIUS server.
- Integrate network devices: Configure network devices (routers, switches, etc.) to communicate with the RADIUS server.
What Are the Key Benefits of Using RADIUS Authentication with Active Directory?
The benefits of using RADIUS authentication with Active Directory include:
- Improved Security: By centralizing user authentication, organizations can enforce stringent access controls and reduce the risk of unauthorized access.
- Streamlined User Management: IT teams can add, modify, or delete user accounts from Active Directory, which automatically reflects in RADIUS authentication.
- Flexibility: RADIUS supports various authentication methods, including EAP (Extensible Authentication Protocol) and PEAP (Protected Extensible Authentication Protocol).
- Scalability: Organizations can easily scale their authentication process as they grow, accommodating more users without compromising security.
What Challenges Might Organizations Face During Implementation?
While integrating RADIUS authentication with Active Directory can provide significant benefits, organizations may encounter some challenges:
- Complex Configuration: Setting up RADIUS and configuring it to work seamlessly with Active Directory can be technically complex.
- User Training: Employees may require training to understand any new authentication processes or changes.
- Compatibility Issues: Organizations must ensure that all network devices and applications are compatible with RADIUS protocols.
How Can Organizations Overcome These Challenges?
To address these challenges, organizations can take the following steps:
- Engage IT experts or consultants to assist with the setup and configuration process.
- Provide comprehensive training programs for employees to familiarize them with the new system.
- Conduct thorough testing to ensure compatibility across all devices and applications before full deployment.
What Role Does Monitoring and Auditing Play in RADIUS Authentication?
Monitoring and auditing are critical components of RADIUS authentication with Active Directory. By continuously tracking user activities and access attempts, organizations can identify and mitigate security risks. Key aspects include:
- Real-Time Monitoring: Keep an eye on user access patterns and detect anomalies in real time.
- Audit Trails: Maintain detailed logs of user authentication events for compliance and forensic purposes.
- Regular Reviews: Conduct periodic reviews of user accounts and access privileges to ensure they remain appropriate.
What Are the Future Trends in RADIUS Authentication with Active Directory?
The future of RADIUS authentication with Active Directory is likely to be influenced by several trends, including:
- Increased Adoption of MFA: Multi-factor authentication will become more prevalent to enhance security.
- Cloud Integration: More organizations will look to integrate RADIUS with cloud-based services and applications.
- AI-Powered Security: Artificial intelligence will play a role in identifying and responding to potential threats in real-time.
Conclusion: Is RADIUS Authentication with Active Directory Right for Your Organization?
In conclusion, RADIUS authentication with Active Directory provides a robust and secure method for managing user access in today's digital environment. By centralizing user management and enhancing security, organizations can protect sensitive data and maintain regulatory compliance. While challenges may arise during implementation, the benefits far outweigh the drawbacks, making this solution a viable option for businesses of all sizes.
Article Recommendations
- What Is Open On Xmas
- The Prince Of Denmark
- Desk Of Donal Trump
- Chuck Drummond Died
- Finalists On Dancing With The Stars
- New Year Movie 2024
- Gypsy Eose Crime Scene
- De Donde Es La Mama De Donal Trump
- Trent Williams Tattoos
- Going Gluten Free Changed My Life